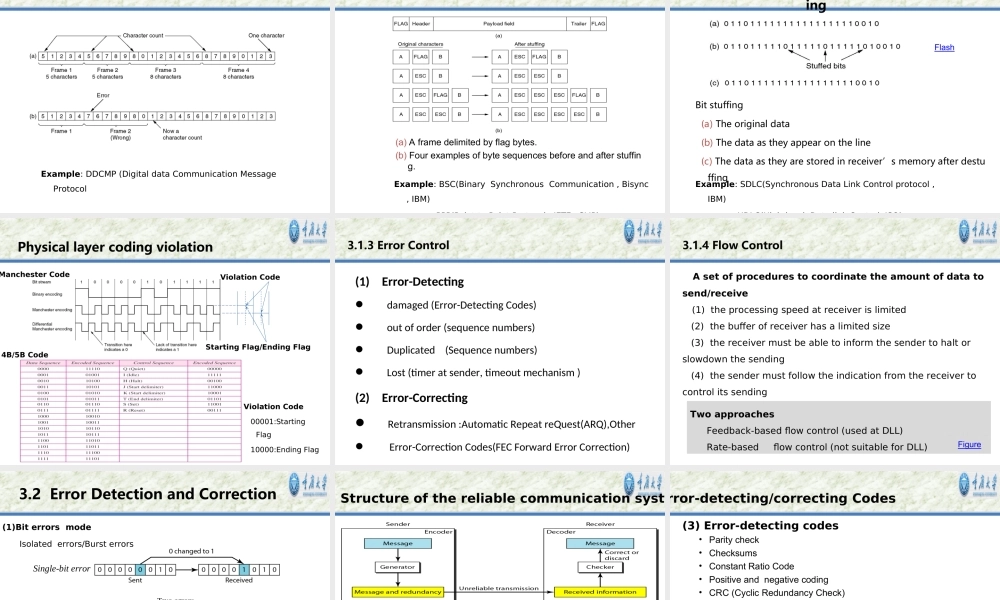
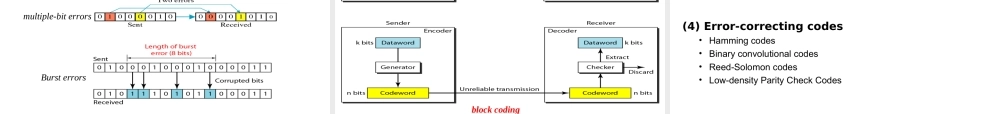
CollegeofComputerScienceChongqingUniversityContents3.0DefinitionandConcept3.1DataLinkLayerDesignIssues3.2ErrorDetectionandCorrection3.3ElementaryDataLinkProtocols3.4SlidingWindowProtocolsandARQS3.5ExampleDataLinkProtocols3.6Summary3.0DefinitionandConceptThedatalinklayerprovidesthefunctionalandproceduralmeanstotransferdatabetweennetworkentitiesandmightprovidethemeanstodetectandpossiblycorrecterrorsthatmayoccurinthephysicallayer,especiallytotransfersdatabetweenadjacentnetworknodesinawideareanetworkorbetweennodesonthesamelocalareanetworksegment.Originally,thislayerwasintendedforpoint-to-pointandpoint-to-multipointmedia,characteristicofwideareamediainthetelephonesystem(1)DataLinkLayerDefinition:(NoISODefinition)Purpose:(2)Link:PhysicalLink3.0DefinitionandConceptNode:hosts,switches,bridges,routersLink:communicationchannelsthatconnectadjacentnodesalongcommunicationpatharelinks–wiredlinks–wirelesslinks–LANs“link”data-linklayerhasresponsibilityoftransferringdatagramfromonenodetoadjacentnodeoveralink(3)DataLink:LogicalLink(4)Frame:Header+Payload(DataFromUpperLayer)HostAHostBNode1Node2Node3UpperLayerProtocolsDataLinkLayerProtocolDataLinkLayerProtocolDataVirtualChannelDataVirtualChannelDataActualChannelDataActualChannelDataLink/LogicalLink=(Physical)Link+DataLinkLayerProtocol3.0DefinitionandConcept3.0DefinitionandConceptPlacementofthedatalinkpaotocol3.1DataLinkLayerDesignIssuesNo.Issues/FunctionsMemo1ServiceProvidedtoTheNetworkLayers2Framing3ErrorControlHandletheErrorsProducedByPhysicalLayer4FlowControlRateMatchbetweensenderandReceiver5TransparentTransmissionHowtohandlethecontrollinginformationinpayloads6LinkmanagementConnection-OrientedCommunication7AddressingBroadcastChannel,ShareChannel8OtherIssuesShareChannel:MediaAccessStrategy/Mode3.1.1ServicesprovidedtoTheNetworkLayer(1)Unacknowledgedconnectionlessservice(2)Acknowledgedconnectionlessservice(3)Acknowledgedconnection-orientedserviceConcept(1)Acknowledgedvs.Unacknowledged(2)Connection-orientedvs.ConnectionlessFeatu...