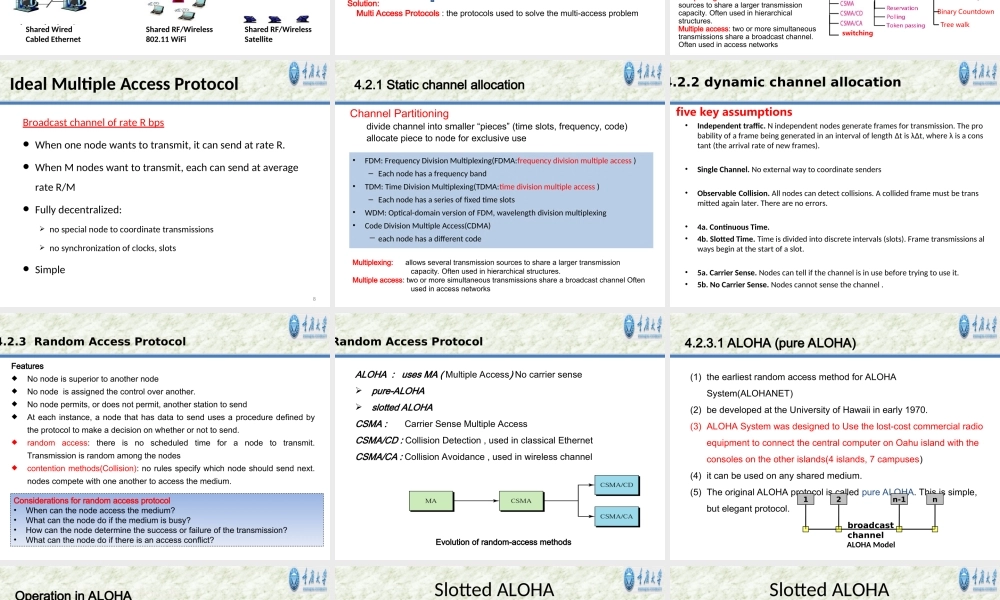
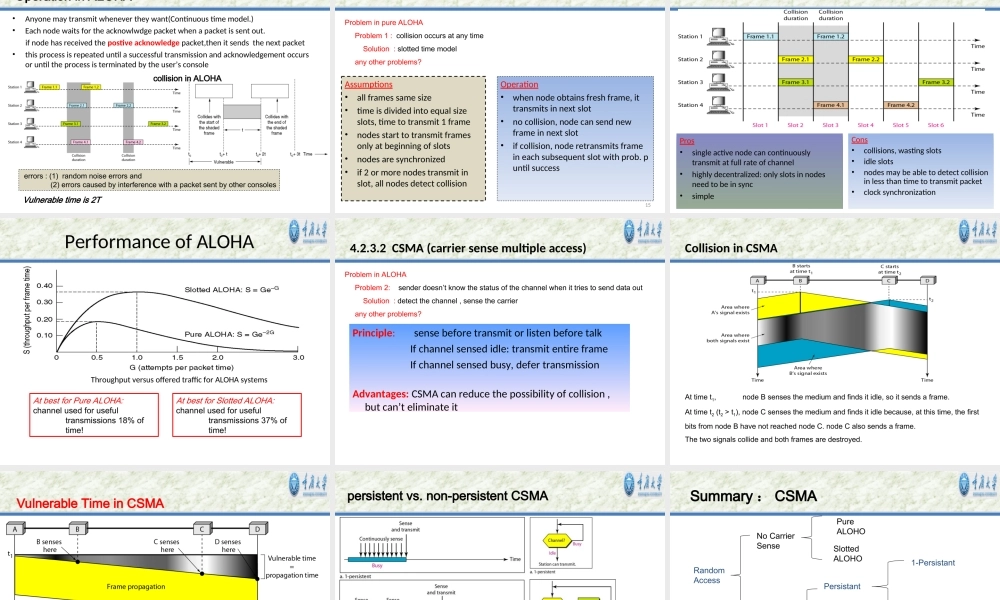
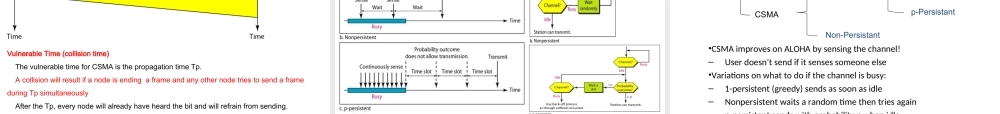
CollegeofComputerScienceChongqingUniversityMediumAccessControl•Networkscanbedividedintopoint-to-pointconnectionsandmultiaccess(broadcast)channels.Inbroadcastnetwork,thekeyissueishowtodeterminewhogetstousethechannel.TheprotocolsusedtodeterminewhogoesnextonamultiaccesschannelbelongtoasublayerofthedatalinklayercalledtheMAC(MediumAccessControl)sublayer.-介质访问(控制)子层TheMACsublayerisespeciallyimportantinLANs,manyofwhichuseamultiaccesschannel.WANs,incontrast,usepoint-to-pointlinks,exceptforsatellitenetworks.TheMACSublayer•Responsiblefordecidingwhosendsnextonamulti-accesslink–Animportantpartofthelinklayer,especiallyforLANsPhysicalLinkNetworkTransportApplicationMACisinhere!Contents4.1TheChannelAllocationProblem4.2MultipleAccessProtocols4.3Ethernet4.4EthernetSwitchtechnology4.5WirelessLANs4.6Summary4.1TheChannelAllocationProblemSharedWiredCabledEthernetSharedRF/Wireless802.11WiFiSharedRF/WirelessSatelliteRadiofrequencyisasharedmedium,multipleusersareusingthesamespectrum(e.g.800-825MHz)NetworkLinks(1)point-to-pointLink(2)multiaccess(broadcast)channels,sharedwireormediumFeaturesofbroadcastchannels(1)asinglesharedchannelisusedbyallnodes,multiplesendingandreceivingnodes(2)twoormoresimultaneoustransmissionsbynodes:interference-collisionifnodereceivestwoormoresignalsatthesametime(3)usually,allnodesareequaltoeachotherThemulti-accessproblem:Inasinglechannelbroadcastnetwork,Whenmultiplenodestrytosendmessagessimultaneously,whohastherighttousethechannel?Solution:MultiAccessProtocols:theprotocolsusedtosolvethemulti-accessproblemThemulti-accessproblem:Howtoletdistributedusers(efficiently)shareasinglebroadcastchannel?Themulti-accessproblem:Howtoformaaccessqueuefordistributedusers?Thequeueingtheorycanbeusetoefficiencyofvariousmulti-accessprotocolsThemulti-accessProblemMultipleaccessprotocolsFDMATDMACDMAControlled-accessprotocolStaticmodelDynamicmodelWDMAswitchingRandomAccessProtocolMultiplexingallowsseveraltransmissionsourcestosharealargertransmissioncapacity.Oftenusedinhiera...